Hash & Encryption Calculator
5.0Penilaian
Nov 02, 2024Pembaruan Terbaru
1.0Versi
Cara menginstal file .IPA
Bagikan
Tentang Hash & Encryption Calculator
Encryption became a common thing with the availability and spread of information we’re facing today, encryption of various kinds has to be employed if we want to ensure any level of information confidentiality. Hashing is a method of checking the integrity of encrypted content and lets us detect any and all modifications done to it.
Features:
• Instance check with type MD2, MD4, MD5, SHA 1, SHA 224, SHA 256, SHA 386, SHA 512, Base 64, ROT13.
• Copy Paste Result.
• User friendly Interface and Navigation.
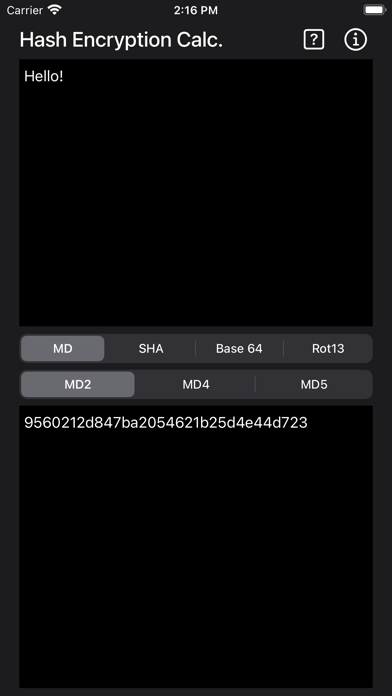
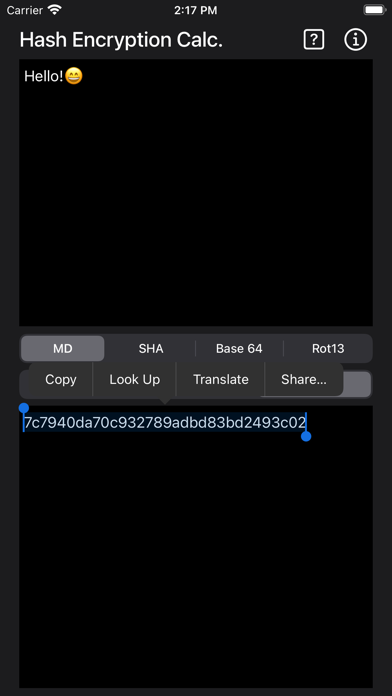
MD5
Complete an MD5 output on the Input data using the MD5 Message-Digest Algorithm. This algorithm is a hash function that produces a 128-bit 16-byte hash value. Useful for security application, it can perform a check data integrity function. It was designed to replace MD4. Typically, it is expressed as a hex number that is 32 digits long. As it is not collision resistant, it is not good for digital signature or SSL certificate applications.
Hash keying is also known as convergent encryption. This keying and encryption is a cryptosystem that produces ciphertext from plain text.
A cryptographic hash function is an algorithm that takes data and provides a hash value. The message or value to be encoded is the data while the hash value is called a digest or message digest.
Authentication and digital signatures are two of many information security applications involving cryptographic hash. The hash functions can also be useful for fingerprinting, identification of duplicate data, detection of data corruption, and creation of hash tables. Cryptographic hash values are sometimes called hash values or checksums or digital fingerprints. Security provided by a hash algorithm depends on it being able to produce a unique value. A collision occurs when you get the same hash value for different data. A strong hash value is resistant to computational attacks.
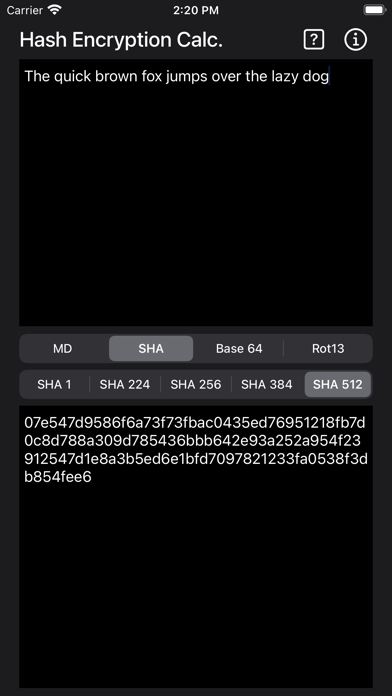
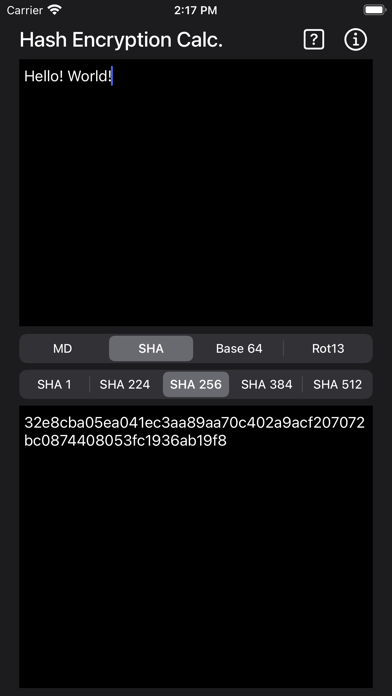
SHA
Complete a SHA output on the data in the Input window choosing from Sha-1, Sha-224, Sha-256, Sha-384, or Sha-512. This set of cryptographic hash functions was designed by the US National Security Agency (NSA) and published in the early 2000’s.
Short for Secure Has Algorithm, the Sha function is an algorithm that hashes data such as a text file into a fixed length variable know as a has. This computed hash value is then used to verify copies of the original data. You cannot recreate the original from the hash value. The SHA functions include digests for 224, 256, 384, or 512 bits.
Hash keying is also known as convergent encryption. This keying and encryption is a cryptosystem that produces ciphertext from plain text.
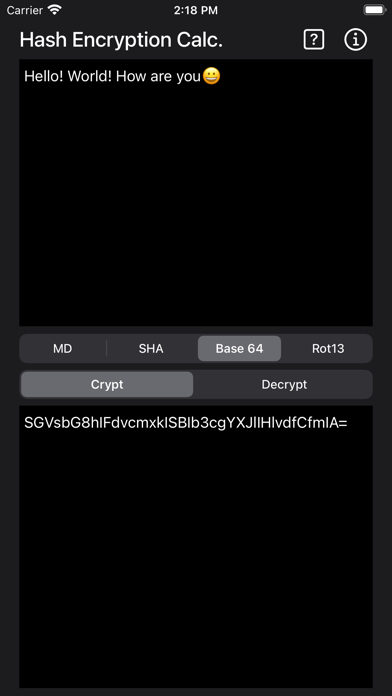
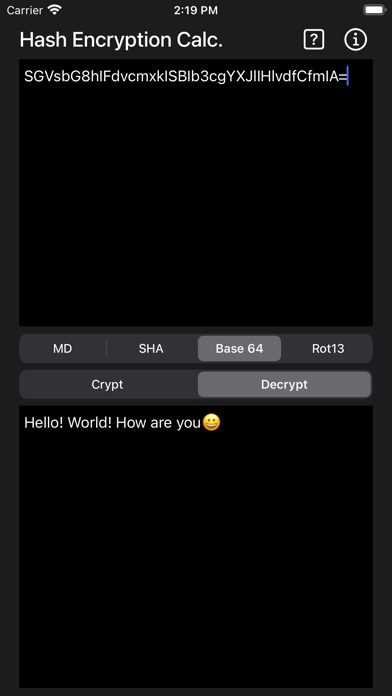
Base64
Base64 is a group of schemes that encode binary to text. This represents binary data in an ASCII strong format. Translation is done via radix 64. The term comes from a MIME encoding. These schemes are typically used when you need to encode binary data stored over media that deals with textual data. Data remains intact with no modification during transport. Email via MIME is one application. Storing data in XML is another application. Encoding that is now called MIME Base64 was first used in a standardized way was through privacy-enhanced mail using the PEM protocol in the mid 1980’s. PEM uses a Base64 scheme that transforms octets to a format of 60bit characters that can use SMTP.
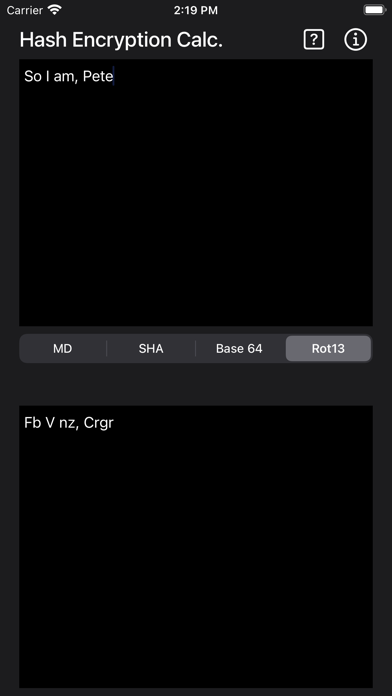
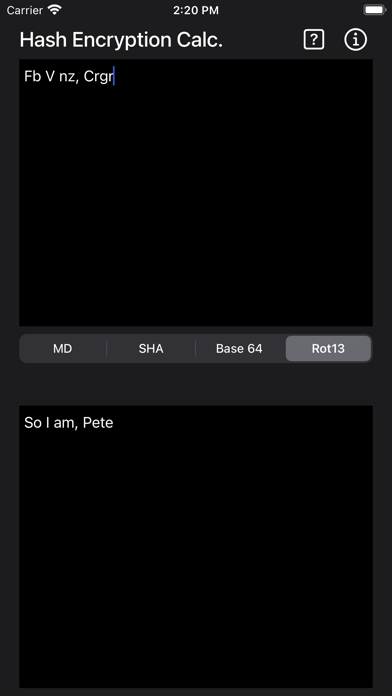
ROT13
("rotate by 13 places", sometimes hyphenated ROT-13) is a simple letter substitution cipher that replaces a letter with the 13th letter after it, in the alphabet. ROT13 is a special case of the Caesar cipher, developed in ancient Rome.
Because there are 26 letters (2×13) in the basic Latin alphabet, ROT13 is its own inverse; that is, to undo ROT13, the same algorithm is applied, so the same action can be used for encoding and decoding. The algorithm provides virtually no cryptographic security, and is often cited as a canonical example of weak encryption.
Thanks for your support and do visit nitrio.com for more apps for your iOS devices.
Features:
• Instance check with type MD2, MD4, MD5, SHA 1, SHA 224, SHA 256, SHA 386, SHA 512, Base 64, ROT13.
• Copy Paste Result.
• User friendly Interface and Navigation.
MD5
Complete an MD5 output on the Input data using the MD5 Message-Digest Algorithm. This algorithm is a hash function that produces a 128-bit 16-byte hash value. Useful for security application, it can perform a check data integrity function. It was designed to replace MD4. Typically, it is expressed as a hex number that is 32 digits long. As it is not collision resistant, it is not good for digital signature or SSL certificate applications.
Hash keying is also known as convergent encryption. This keying and encryption is a cryptosystem that produces ciphertext from plain text.
A cryptographic hash function is an algorithm that takes data and provides a hash value. The message or value to be encoded is the data while the hash value is called a digest or message digest.
Authentication and digital signatures are two of many information security applications involving cryptographic hash. The hash functions can also be useful for fingerprinting, identification of duplicate data, detection of data corruption, and creation of hash tables. Cryptographic hash values are sometimes called hash values or checksums or digital fingerprints. Security provided by a hash algorithm depends on it being able to produce a unique value. A collision occurs when you get the same hash value for different data. A strong hash value is resistant to computational attacks.
SHA
Complete a SHA output on the data in the Input window choosing from Sha-1, Sha-224, Sha-256, Sha-384, or Sha-512. This set of cryptographic hash functions was designed by the US National Security Agency (NSA) and published in the early 2000’s.
Short for Secure Has Algorithm, the Sha function is an algorithm that hashes data such as a text file into a fixed length variable know as a has. This computed hash value is then used to verify copies of the original data. You cannot recreate the original from the hash value. The SHA functions include digests for 224, 256, 384, or 512 bits.
Hash keying is also known as convergent encryption. This keying and encryption is a cryptosystem that produces ciphertext from plain text.
Base64
Base64 is a group of schemes that encode binary to text. This represents binary data in an ASCII strong format. Translation is done via radix 64. The term comes from a MIME encoding. These schemes are typically used when you need to encode binary data stored over media that deals with textual data. Data remains intact with no modification during transport. Email via MIME is one application. Storing data in XML is another application. Encoding that is now called MIME Base64 was first used in a standardized way was through privacy-enhanced mail using the PEM protocol in the mid 1980’s. PEM uses a Base64 scheme that transforms octets to a format of 60bit characters that can use SMTP.
ROT13
("rotate by 13 places", sometimes hyphenated ROT-13) is a simple letter substitution cipher that replaces a letter with the 13th letter after it, in the alphabet. ROT13 is a special case of the Caesar cipher, developed in ancient Rome.
Because there are 26 letters (2×13) in the basic Latin alphabet, ROT13 is its own inverse; that is, to undo ROT13, the same algorithm is applied, so the same action can be used for encoding and decoding. The algorithm provides virtually no cryptographic security, and is often cited as a canonical example of weak encryption.
Thanks for your support and do visit nitrio.com for more apps for your iOS devices.
Tangkapan layar Hash & Encryption Calculator
Hash & Encryption Calculator FAQ
Bagaimana cara mengunduh Hash & Encryption Calculator dari PGYER IPA HUB?
Apakah Hash & Encryption Calculator di PGYER IPA HUB gratis untuk diunduh?
Apakah saya memerlukan akun untuk mengunduh Hash & Encryption Calculator dari PGYER IPA HUB?
Bagaimana cara melaporkan masalah dengan Hash & Encryption Calculator di PGYER IPA HUB?
Apakah Anda menemukan ini membantu
Ya
Tidak
Paling Populer
Sing It - Ear TrainerA must app for every musician, singer, or just for fun.
Test,train, and improve your musical ear an
Tube PiP - PiP for YouTubeTube PiP - the ultimate YouTube companion for iOS:
1. Picture in Picture (PiP) Playback: Watch YouT
Papaya Ouch!In the game Papaya Ouch!, you can experience backpack management, tower defense, TD, merge, match 2,
Lets Go VPNLets Go VPN, the most advanced VPN, is designed by a team of top developers who strive to ensure all
Paprika Recipe Manager 3Organize your recipes. Create grocery lists. Plan your meals. Download recipes from your favorite we
War Pigeons UnboundedWar is coming. Deep down in top secret military labs they have evolved, mutated - and escaped. The f
Procreate PocketApp of the Year winner Procreate Pocket is the most feature-packed and versatile art app ever design
Cowboy Westland survival runAre you ready to take part in the #1 exciting 3D western adventure? Cowboy Westland survival run mak
Max: Stream HBO, TV, & MoviesIt’s all here. Iconic series, award-winning movies, fresh originals, and family favorites, featuring
TonalEnergy Tuner & MetronomeFor musicians from pros to beginners, whether you sing, play a brass, woodwind or stringed instrumen
SkyView®SkyView® brings stargazing to everyone. Simply point your iPhone, iPad, or iPod at the sky to identi
Ninja Dash 2015Ninja Dash 2015 is the fast paced running game!<br>On these maze fields, rush to the end of this nin
Tami-Live Chat&VideoTami is an app that records daily life and ideas.<br><br>You can use it to record your every day, wh
SALE Camera - marketing camera effects plus photo editorSALE Camera Help you create the best Business to consumer Stock Photos and Images. provides 300 filt
DevTutor for SwiftUI"DevTutor" is an application designed to assist developers in creating exceptional apps using SwiftU
Mokens League SoccerDive into Mokens League Soccer and experience the new era of soccer gaming!
Esports for Everyone: W
Zombie ZZOMBIE ENDLESS RUNNER LIKES NO OTHER!<br><br>WHY?<br><br>* Awesome graphic quality!<br><br>* Simplif
Dead Z - Zombie SurvivalCatastrophic explosion at the Omega Labs started the apocalypse, now spreading across the Earth.
Ta
HotSchedulesHotSchedules is the industry's leading employee scheduling app because it’s the fastest and easiest
ChatGPTIntroducing ChatGPT for iOS: OpenAI’s latest advancements at your fingertips.
This official app is
Disney StoreDisney Store is your official home for exclusive collections, designer collaborations, and one-of-a-
fight back tennisa Pong game with Tennis style, the gameplay itself is very simple, you can using Touch. Ball speed w
Dr. Mina AdlyMina Adly mobile app provides students with portable instant access to a selection of services.
Usi
iVerify BasiciVerify Basic is your gateway to enhanced device security and threat awareness, offering a glimpse i